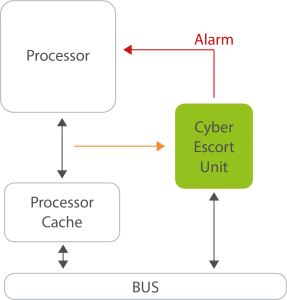
Cyber Escort Unit IP
Bridging Software and Hardware Security Gaps
The Cyber Escort Unit is designed to fill the security gap between software cybersecurity and hardware by escorting step by step the program execution to achieve high execution performances in a secure way, allowing advantageously real-time detection of zero-day attacks. Unique on the market, this product builds the foundation for hardware-enabled cybersecurity.
It is the only tool on the market that comprises technologies for detecting and deterring cyberattacks. This technology acts on-the-fly. Precisely, Secure-Call is aiming to protect against the four threats which represent a large number of vulnerabilities encountered in practice.
- Return oriented programming (ROP): The attacker reuses chunks of code to assemble a malicious program like a patchwork.
- Stack Smashing, by exploiting a buffer over run or integer under-or-overflow etc.: the attacker crafts some fake stack frames in order to change the program context.
Cyber Escort Unit IP offers the following features:
- Real-time detection of Zero-Day attack by monitoring step by step the program execution
- Stops the attack before it is execute
- Compared to SW level cyber protection, it cannot be exploited remotely, as it is inaccessible to an attacker
- Ensures protection against Fault Injection Attack (Temperature, Electromagnetic Injection, Clock Glitch, Power Glitch, Laser Injection) an Software Cyber Attack (Code Injection, Buffer Overflow, Stack Smashing, Control Flow Graph hijacking, 0-day attacks targeting SW execution)
- Allows to limit false positive alarms as it is checking fundamental properties of well-behaved cod
- No processor modification
- Runtime impact highly limited (<1% in most cases)
- Low hardware footprint
- Agnostic for the program
Cyber Escort Unit IP can be used in several markets and applications such as automotive (real time, low latency requirement, safety compatible), SCADA (supervision), datacenter (data protection), network and telecom infrastructures and government sector (incl. defense and aerospace).
Cyber Escort Unit is particularly relevant for:
- Detecting all return address corruption on the stack
- No impact on computation time
- Very easy set-up
- No recompilation needed, no influence on the protected program
- Can be used in a safety context, i.e., restore PC, so that the system comes back to a stable stat