Physically Unclonable Function (PUF) IP
A Physically Unclonable Function (PUF) is a security mechanism that uses the inherent physical variations of a device to generate a unique, unclonable output.
This output can be used as a cryptographic key or a device identifier. PUFs rely on the fact that the exact physical properties of a device, such as the physical and electrical characteristics on a chip, can never be replicated exactly. This makes PUFs a highly secure method for protecting sensitive information and ensuring device authenticity. PUFs are often used in a wide range of applications, including secure boot, secure storage, and secure key generation.
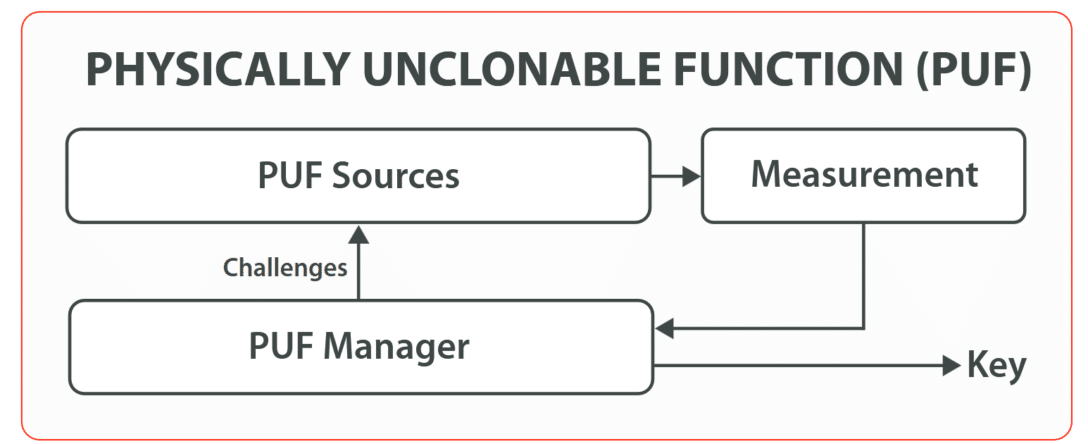
PUF IP Core is a secret key generation system based on Physically Unclonable Functions (PUF). The secret key is extracted by the PUF from the silicon by using its inherent properties: technological dispersions are amplified into digital signals (bits of information). The key generated by the PUF is not readable but extracted using a group of helper-data. This distinctive feature allows a real protection against the reverse-engineering techniques compared to traditional methods that store the key in non-volatile memory.
In order to have a good PUF, many properties must be taken into account such as:
- Randomness, which indicates the balance of 0 and 1
- Steadiness, which indicates the stability with which a PUF produces the same responses to the same sets of challenges.
- Diffuseness, which indicates the degree of difference between the IDs generated from the different challenge sets in the same PUF
- Uniqueness, which indicates how different the generated IDs are.
- Tamper resistance
- Mathematical Unclonability
- Physical unclonability
But also, Security metrics such as:
- Entropy = 128.0 bit for a typical AES-128 key
- Reliability = fixed to the desired value, e.g., 1 FIT for ASIL D
- Entropy & reliability ensured in all specified corners (owing to adaptive control, a unique feature of our PUF)
Physically Unclonable Functions (PUFs) are being used in various markets (examples) such as
- Information security
To secure digital devices by generating unique and unpredictable identifiers, which can be used for authentication, encryption, and access control. - IoT
To secure IoT devices, such as smart home systems, wearable devices, and industrial sensors, by providing unique and unclonable identities and preventing unauthorized access. - Automotive
Used in automotive systems to secure access to critical components, such as engine control units, and prevent tampering and reverse engineering. - Healthcare
To secure medical devices, such as pacemakers and insulin pumps, to prevent unauthorized access and protect sensitive patient
information. - Banking and finance
Used in payment systems and financial services to secure transactions and prevent fraud. - Government and military
Used in government and military systems to secure sensitive information and protect against cyber attacks.
Credential generation
The PUF IP ensures credential generation based on process variations properties which are unique from chip to chip, impossible to reproduce or emulate, hence alleviating the problem of external key management system and can be used for several use-cases, detailed hereafter:
- Generation of a unique identity for a semiconductor device
- Anti-tamper key protection against cloning or reverse engineering
- Chip sample authentication using a challenge response protocol
- Firmware authentication (integrity + genuine origin) using the generated key
- Firmware encryption (unique per device, which pairs a code with a device, thereby denying attack-one-break-all attacks) using the generated key